Why have a SOC when you have an IT Dept.?

AUTHORED BY CHAMOD WIJETUNGE & WARUNA SAMPATH SAMARAWEERA
Why have a SOC when you have an IT Dept.?
Nowadays, organizations must look for strong countermeasures to struggle with real-world cyber threats such as cyber-attacks and data breaches which are increasing rapidly. Even the most sophisticated companies struggle with protecting their data.
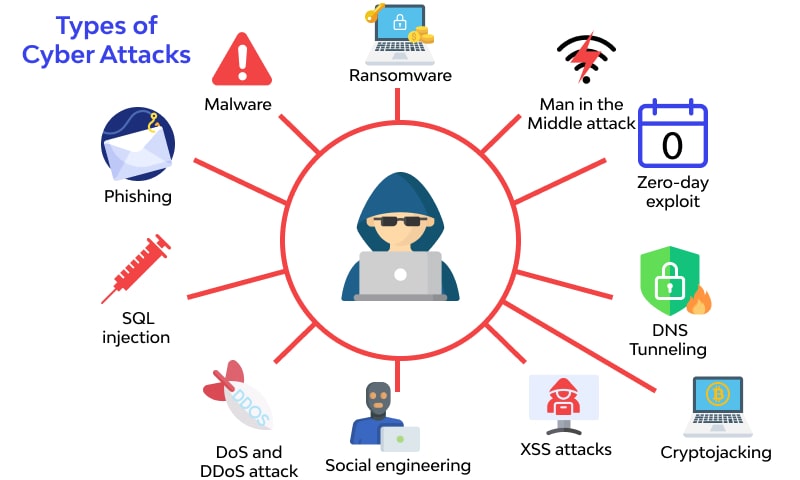
The best solution we can provide to safeguard your organization is establishing a Security Operations Center (SOC). It is the famous frontline of cyber defence nowadays. Organizations with different business models and domains rely on them to react to threats. This is simply because a team will be responsible for all IT issues at an organization, whether they are cybersecurity threats or potential risks.

WHAT IS AN SOC
According to Gartner, a SOC is defined as follows: “A security operations center (SOC) can be defined both as a team, often operating in shifts around the clock, and a facility dedicated to and organized to prevent, detect, assess and respond to cybersecurity threats and incidents, and to fulfill and assess regulatory compliance.”
The Security Operation Center (SOC) is a centralized role within an organization that uses people, procedures, and technology to continuously monitor and enhance the business’s security posture while preventing, detecting, analyzing, and responding to cybersecurity incidents.
A SOC functions as a hub or central command post, collecting telemetry from across an organization’s IT infrastructure, including networks, devices, appliances, and data stores, wherever they may be. The development of advanced threats necessitates gathering context from a variety of sources. Essentially, the SOC serves as the point of contact for any events logged within the organization that is being monitored. The SOC must decide how each incident will be controlled and dealt with.
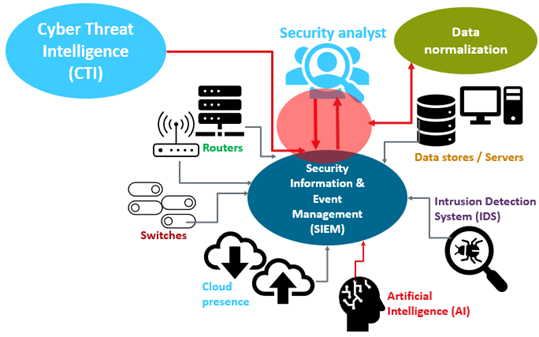
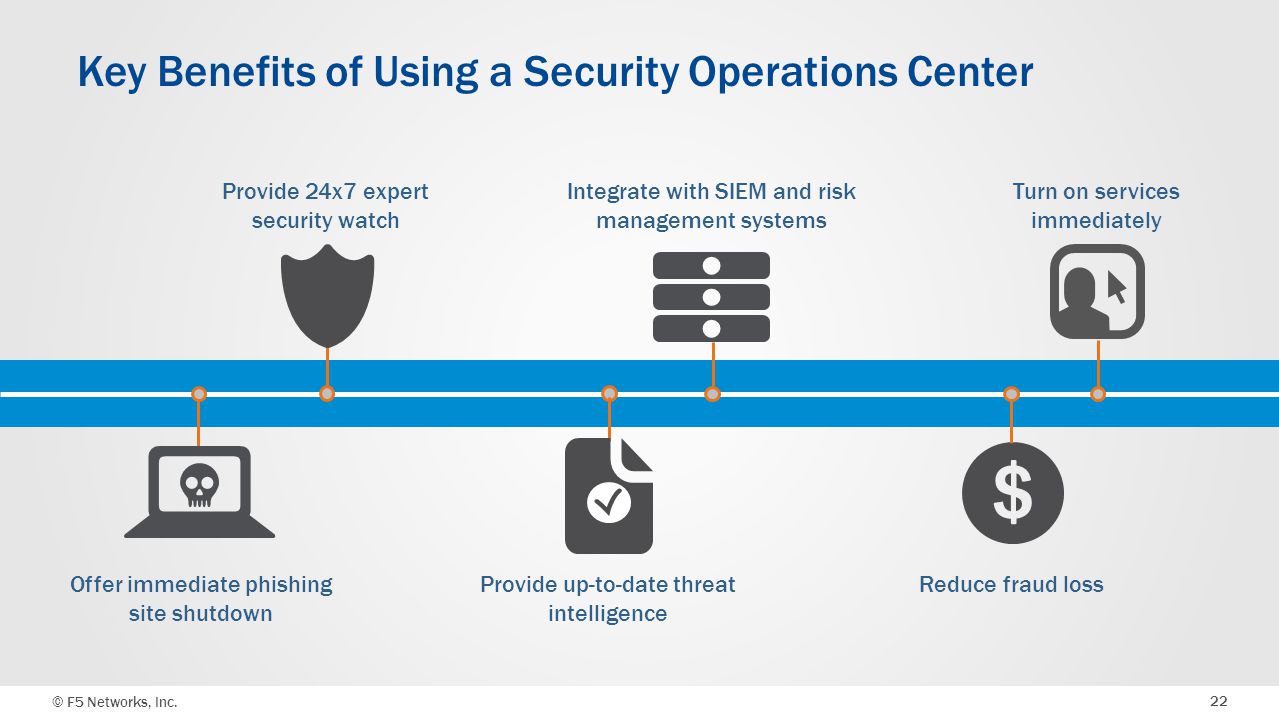
What are the significant benefits of implementing a SOC?
Establishing a SOC (security operations center) is a big task. However, it is well worth it when adequately configured to provide better security for your organization. Creating a SOC requires careful planning and coordinating people, processes, and technologies. A functional SOC will have the necessary capabilities to assist your organization’s security in today’s threat landscape. Let’s look at some of the benefits that organizations will have after implementing a SOC:
- A dedicated team of experts responds instantly to the reported/identified threats.
- SOC would have a defence plan to protect better and prevent any attacks that occur.
- A SOC can mitigate any potential damage from an attack on your organization.
How Do SOCs Work?
The main goal of a SOC is to monitor the security incidents of the organization and alert you if there is any potential danger occurs. To achieve this, SOCs collect massive amounts of data regarding your organization to understand how threats may attack.
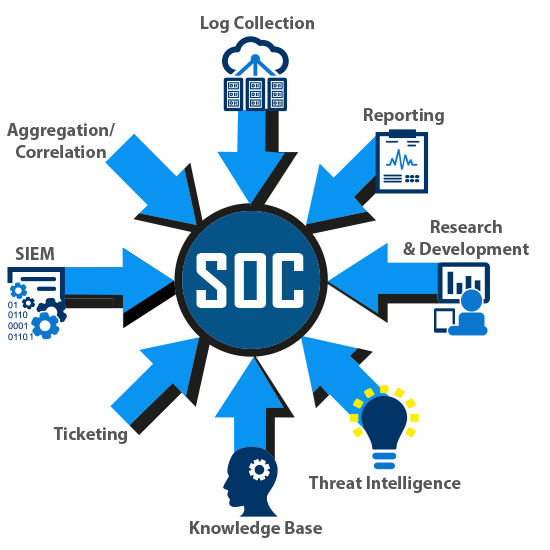
SOCs utilize special software and threat intelligence platforms to collect and analyze data. Typically, SOCs will monitor hardware and software. Then when threats, inconsistencies, or abnormal trends appear, the SOC team will act.
A SOC checks all systems and infrastructure for potential abnormalities. SOC analysts collect data and conduct monitoring, which we call “asset discovery.” Here the SOC builds a deep understanding of all the technologies used within the organization and monitors them for security issues.
Additionally, suspicious activity is also monitored. The SOC records will also track employees accessing suspicious websites or downloading unnecessary software.
Understanding network activities and communications are also crucial for an organization. When implementing a SOC, also we look for them. Tracking email and other sources of communication are vital for ensuring that the company is secure. Furthermore, this tracking loop back into behavioural monitoring principles.
As you can see, much of SOC’s work is preventative. However, if an incident occurs, the SOC team will jump into action and take active measures. This part is known as incident response. Incidence response refers to any sort of security compromise that occurs.
An incident can range from a severe impact attack to a security risk being discovered. The SOC then ranks incidents as they occur, investigates them, and determines their root cause. These steps help ensure that the incident does not repeat and prevent hackers from breaking the organizational network using backdoors.
Lastly, a SOC can also help your organization maintain regulatory compliance. Using AI technologies to monitor network traffic, your SOC can alert you to potential regulatory violations that may occur when sensitive data is shared with the wrong people. SOCs play a vital role in protecting the integrity of your organization and ensuring that sensitive data does not fall into the wrong hands.

N-able and SOC
Minimizing these potential threats, N-able will provide security services for telecommunication, BFSI, Government, and Enterprise customers using their Security Operation Centers (SOC). We have capabilities to identify the real-time threats in the customer environment and provide 24*7 monitoring support with the solutions. When engaging with us, N-able will provide “All your security needs under one roof”. If you would like to know more about how we can help your business with an SOC or relates security solutions, write to us on This email address is being protected from spambots. You need JavaScript enabled to view it.
